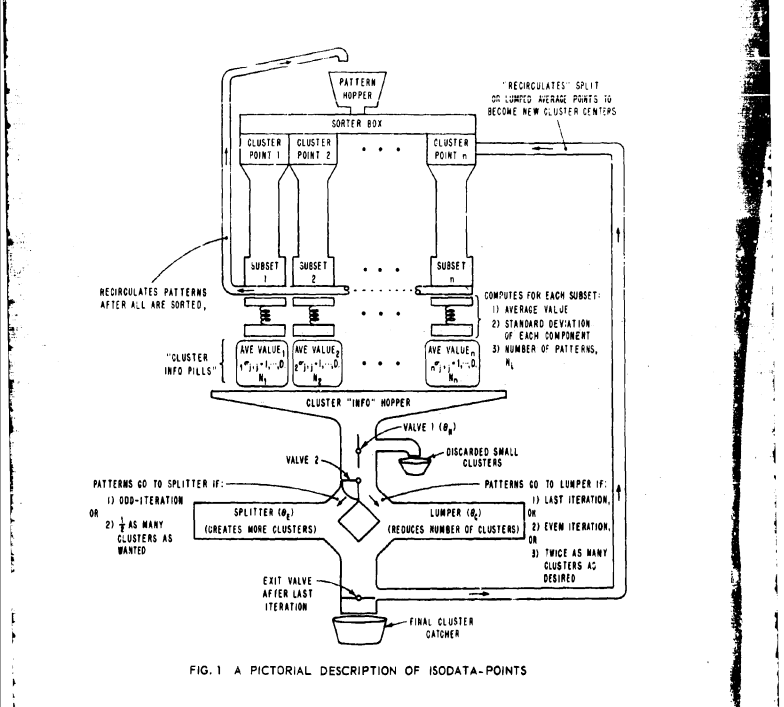
I love how this illustration uses symbols and terminology from what I suppose is mechanics to describe the functioning of an algorithm.
Make sure you have an environment variable pointing to your home directory (or rather the directory where your _netrc file is).
This one caught me a bit off guard. It turns out UNION in TSQL really is the mathematical union of the two result sets not just the concatenation of the involved results.
Include the keyword ALL to ensure duplicates are also returned.
ALL
Incorporates all rows into the results. This includes duplicates. If not specified, duplicate rows are removed.
- Transact-SQL reference
It seems that you can’t configure Apache to support the anonymous-clone authenticated-push scenario over the http-backend.
http://git.661346.n2.nabble.com/git-http-backend-and-Authenticated-Pushes-tp4703506p4703506.html
Fortunately the situations where I need anonymous access are rather limited (TeamCity does not support authentication over http for git). I was able to solve it by serving repositories without authentication under a different url like so:
ScriptAlias /git/ “C:/Progra~1/Git/libexec/git-core/git-http-backend.exe/”
ScriptAlias /_git/ “C:/Progra~1/Git/libexec/git-core/git-http-backend.exe/”
This after figuring out how to make TeamCity accept our selfsigned certificate.
You can run into quite strange errors when attempting to access WMI though ASP, note that there are a few steps to remember for bliss.
- Ensure you give permissions for the user in question to access WMI. Computer -> Manage -> Configuration -> WMI Control -> Properties, in the Security tab ensure your user has permissions to the right namespaces (probably Root/CIMV2). The permission required is usually
- Use either SC.exe or preferrably SetACL.exe to set access control lists for the relevant user on the service, for example:
SetACL.exe -on SERVICE_NAME -ot srv -actn ace -ace "n:USER_OR_GROUP;p:start_stop"
- Finally you need to enable impersonation to work, for that we need to pass the password as plaintext. To do this ensure you use Basic authentication instead of Windows Authentication.
